Online Privacy | Where are they watching and what do they know?

We live in an always connected world. But how many of us see online privacy as a priority?
Most of the time we don't think anything of connecting to the internet to do any number of tasks. Shopping, social media, work, banking, entertainment, the internet has become an everyday tool for most people in America.
For many people, online privacy isn't an issue given much thought, but a rising number of people are falling victim to identity theft and bank account fraud.
Now, add to this what we know about NSA surveillance, and we have some serious reasons to want to protect our online privacy
This guide will explain some of the biggest online threats to our privacy, how they are used against us, and what we can do to fight them.
Home network privacy
A wireless router is a staple appliance in most households in the US. People love the convenience of wireless, and the portability of today’s devices. What many users don’t realize is that this convenience can come at a high cost to privacy. If you care about your home network privacy, we strongly recommend looking into VPN router options such as the Netgear R7000 or Asus RT-AC56U.
In 2008, Wifi Protected Setup (WPS) was introduced. WPS was designed to allow for easy setup and connection by allowing a button on the router to push login information to a device. This meant administrators didn’t have to remember passwords. While good in theory, WPS is a security nightmare and puts your network at risk.
Many security experts have demonstrated the weaknesses in WPS that allow the passphrase to be revealed, and just how easy it could be to crack the password.
The reality is that even low level hackers can force a WPS connection without physical access to the router. These hackers can even change the password to the network, effectively locking administrators out of their networks.
Ouch! You might not post your wifi password publicly, but your router is! Clearly this represents a security risk. Your router is handing over the keys to your network to anyone with the skills and knowledge to request access.
Firmware
Even if you were lucky or informed enough not to buy a WPS enabled router, that doesn’t mean you are in the clear. Remember when we said that the router is a staple appliance in most homes?
The problem with appliances, is that we take them for granted. Most people only think of their wireless router when they need to connect online or can't connect. This is the case with utility appliances - we remember to change the lightbulb over the stove when we try to turn it on. Out of sight, out of mind.
The fact is, a router shouldn’t be a set-it-and-forget-it appliance. We might not need to do a security update on our toaster, but we sure do them on our computers.
A 2014 Consumer report from Tripwire found that 59% of people surveyed didn't have up to date firmware on their routers, and 68% of people didn't know how to update the firmware.
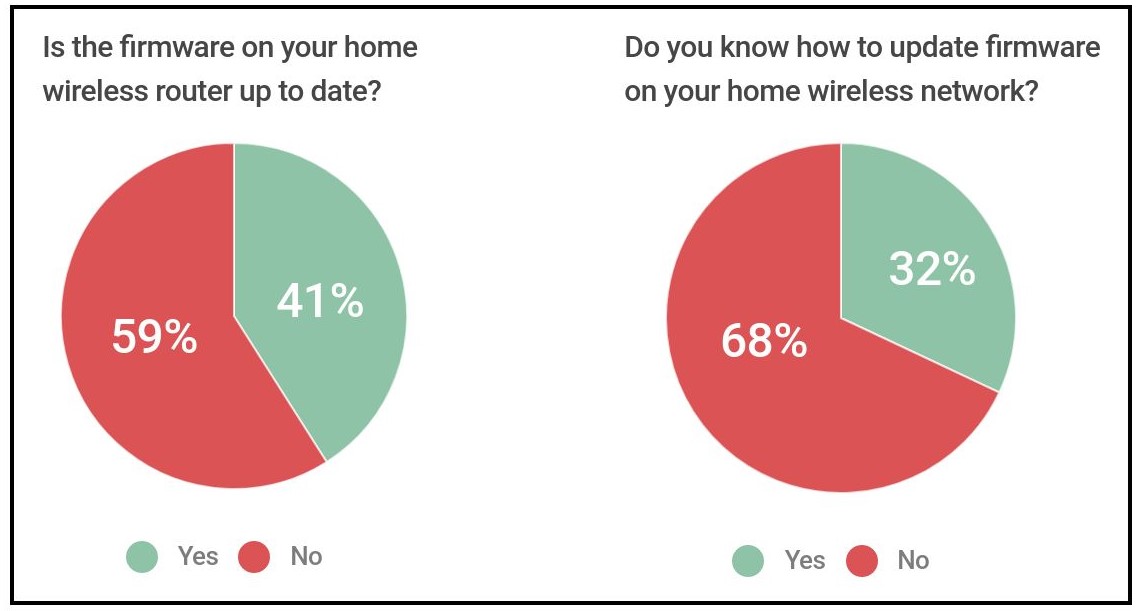
When was the last time you ran a security update on your router?
Usually, the answer is never. Unlike your laptop or desktop that can be set for automatic updates, routers require you to log in, check a website for firmware updates, and manually install the update. As a result, routers almost never get updated from the stock firmware they came with, which is the online privacy equivalent of using a padlock you got in a Christmas cracker to lock your garage.
Until router manufacturers allow for push updates, this problem won’t get fixed.
Our solution?
Just like you have a reminder to check your smoke detector batteries, put a note in your calendar or a reminder on your phone to run a firmware update on your router a few times per year.
Running old, outdated firmware means you are open to attacks and vulnerabilities that have been fixed in later versions of the firmware. You wouldn't run your laptop without updating it, so stop doing it on your router. There are people out there that not only can take advantage of your outdated networking device, but will.
Password
Of course, All of this is pointless if you don't bother securing your wireless network with a sufficient password and security level.
Did you know that most teleco provided routers are set up with your phone number as the password?
Not only should you change your password (and often), you should also be employing the highest standard for encryption, WPA2. (Do not use WEP. It is weak and outdated.)
Consider using a password manager such as KeePass or LastPass to create and store strong passwords, and make sure you have a strong password that you can remember for your main login.
Not your pet's name, not your parent's name, not your kids' names, but something impossible to guess. Try Diceware for a password that's easy to remember yet cryptographically secure.
The takeaway from this article should be that your online security is in your hands. Users who are proactive and make security a priority are at less of a risk. From purchase to everyday use, make informed decisions about your online security and be actively protecting yourself and your family from prying eyes. This article provides additional information on password security.
Public Wifi security concerns
Next we are going to dip our toe into public WiFi.
Twitter, Facebook, Instagram, and a plethora of other social media platforms have taken a foothold in our lives. The result is a constant stream of data that leaves us always on, always connected, always sharing.
One of the ways that we maximize our online access is by using public WiFi spots. Who could have predicted that our online lives would become so prolific that even churches, schools, and doctor’s offices would offer connectivity?

Few people who are online today haven’t used a public WiFi hotspot. Whether it’s at Starbucks or a hotel, we all do it sometimes. But what risk are we taking when we connect over coffee?
Once you are connected to “Bob’s Free WiFi” you can tweet to your hearts content along with everyone else on the network. But, did you know that anyone else connected to that same network could be viewing your online activity?
That email you just sent (the one to your mom with the cat video) can be seen by anyone who chooses to look. And no, we aren’t talking about looking over your shoulder, we are talking about direct access to your network traffic.
Everything you do on public WiFi can be monitored. Whether it is a completely open network or password protected, if you are connected, it is possible for others on the network to view your traffic.
Your banking information is a very personal and private part of your life. Usually, paperwork with banking information on it gets filed or shredded to protect our privacy and identity. But more and more of banking, like everything else in life, is becoming virtual. So, shredding our financial documents is no longer necessary … right?
Logging into online banking is like walking around in your underwear. Best done in the privacy of your home.
If you are viewing your banking information on a public WiFi connection, so might be the rest of the coffee shop.
Forget underwear ... feel naked yet?
For many users, this thought may just not have occurred to them. We are not trained to think about our privacy in a digital world. We lock our doors and windows to keep out intruders and close our blinds to keep out prying eyes but we work on the assumption that our digital lives are hidden behind passwords.
In a study of 2540 people, WiFi access point company Purple discovered that 72% of respondents use public WiFi, and 78% of those actively looked for places that provide it.
What's more alarming, though, is that they also found that 17% of respondents do online banking whilst connected to unsecured WiFi networks, with 87% checking emails, and 27% using it for work purposes.
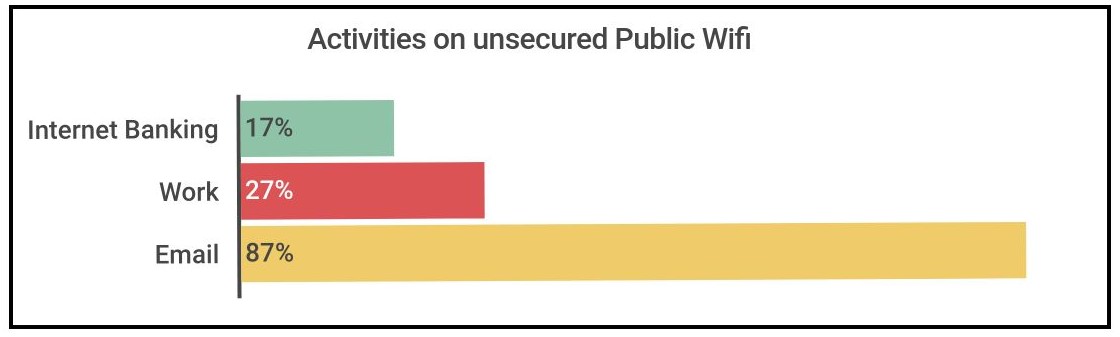
The fact of the matter is that when you are connected to public WiFi, other people can see what you are doing when you are online. Don’t do anything on these networks you wouldn’t want your neighbor to see.
Have no (well, less) fear, there are ways to protect yourself.
The most effective, and super paranoid, way to protect yourself is to just not connect to wireless networks that you do not control. Period.
This means only being online when you are in the privacy of your own home, where you own the network.
Now, once you have taken off your tinfoil hat and decided to rejoin society, there is also a fairly simple option that isn’t quite as extreme.
Use a VPN service. When you are away from home, you can encrypt any data leaving your device by connecting via a VPN. This won’t stop your neighbors from peeking, but it does scramble the information, stopping a possible 'man in the middle' attack. Most VPN providers, like StrongVPN, encrypt this data at the 2048 bit rate. While that might not stop the NSA, it is going to stop the hacker two tables over. Right now, VPN is the best solution out there.
A good rule of thumb: if you were to do the activity on paper, would you want it shredded before you threw it away? If the answer is yes, (or even, maybe) then wait until you get home!
Social media
“Hey just look me up on Facebook!” has become a very common statement in this generation of bits and bytes communication. Droves of people have flocked to social media sites like Facebook, Twitter and LinkedIn by the millions so they can stay informed as to the latest happenings of their friends. Social media allows for rapid communications across the globe whether by gaining new friends on Facebook or possibly landing a new job on LinkedIn, social media thrives through the transfer of information. The question is how does this information put you at risk?
“This rain sucks”
“Looking for a new job. If you know of one hit me up!”
“Five days until I can put my feet in the sand for a week”
“Normally I love my job, but repairing computers in the pouring rain is annoying”
Most people would find these status updates from Facebook as commonplace and ordinary. However one of the biggest threats on the internet lay within the list above. Did you find it? The key here is over sharing information.
The third update in the list should be a red flag. It looks simple enough, but when you take a deeper look you may find something disturbing.
The person that wrote the update in question willingly and voluntarily told all of his friends that they will be away from home for an entire week starting in five days. This is the equivalent of putting a sign in your yard saying, ‘empty house for the next week!’ To add insult to injury, in this case, I clicked on my friends Facebook page and scrolled down just a little ways to learn that he bought a new TV. Oh nice, a brand new TV and an empty house.
Immediately people’s response to the above is, “well they are my friends and they wouldn’t use that sort of info to do me harm”. Hopefully this is the case, but did you know that oftentimes friends of your friends can see what you post? This obviously presents a problem. Now people you don't know - or trust - can see that you will be gone. Luckily, Facebook has a fairly strong privacy control system so you can control what people see on your wall. This is great, except most people do not know, or take the time to learn, how these controls work. If this describes you, go learn … right now.
Privacy on social media
This leads to another issue with social media and your personal security - privacy. Is it even reasonable to expect any privacy when using social media services? In an ideal world perhaps, but in reality, not a chance. While all social media services have a privacy policy you should assume that anything you post or upload will stay private, regardless of your settings.
The issue stems from the fact that, we as users, rely on a third party to protect our privacy online. This trust is placed in the very companies who are using that information we post to sell advertising. How are we to trust anyone who is making money off the very information we are asking them to protect?
If you are anything like me, you have spent a large amount of time blocking game and app request from the likes of Farmville, Mafia Wars, Poker this, Poker that, and - oh my, this would not be a complete list without Candy Crush Saga. While these apps may be fun and extremely addictive, they come at a cost.
Remember when you installed your favorite app and you had to give them permission? Now just what did you give them permission to? Most users don’t know, but assume it must be innocent enough. After all, it’s just a game - right?
Consider the fact that through those permissions, you have just handed over your “private” data to yet another company.
We now know through your status updates that you own a new TV and will be out of town next week. Because you play Candy Crush Saga, now the employees at King Games also know this information about you. Even if you don't play any games on Facebook, your privacy is still at risk. Just take a look at these 7 chilling facts you aren't being told.
Mobile privacy concerns
Most people use their social media services from their mobile devices, without thinking through the effect it may have your online security. The majority of social media sites use some form of geo-location tagging when you update your status, tweet, or upload a picture.
This information can be used to create a map of where you have been, the frequency in which you go to that place, but also where you are at this very moment. This information is just sitting there, being provided by you.
Chain Mail
Remember those “20 things about me” lists that sometimes go around Facebook? Twenty seemingly random questions may seem innocent, but a few can reveal more about a person than they realize.
- What was your most embarrassing moment?
- Have you ever played hooky?
- What was the name of your first elementary school?
- What was your childhood pet’s name?
Looking at this list of questions, you should quickly see one that is familiar. If you have ever set up an online account with security questions, like at a bank or credit company, you have most certainly seen the 3rd question.
Companies use security questions to validate your account in the result of being locked out for a forgotten password. Imagine if this information is sitting out there on social media.
Till death do us part
It is a very common practice for married women to use their maiden names in their profiles, so that childhood friends can find them. No harm in this right? Well what if you and your mother are friends on Facebook? Better yet, you tag your mother as a relative.
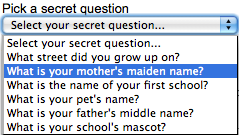
Does the security question, “What is your mother’s maiden name” ring any bells? Unfortunately, seemingly innocent social media interactions can create large security risks in real life.
The big issue
The real problem is not with social media and its privacy policies, but rather that we as users are so willing to trust someone with our most personal information. We are our own biggest threats when it comes to social media use. Information gathered on social media sites are used everyday against people. You can stop the risk by making informed choices and being aware of the information you are giving the world. You have to be diligent about the information you are willing to share, and who you share it with. A good rule of thumb is to assume no privacy and be your own content filter.
ISPs
In order to connect to the the internet you must have an ISP. As inhabitants of the world wide web, we rely on these companies to provide us with the connectivity that we desire. While there are many forms of internet service including dial-up, DSL, cable, and even satellite, one thing is the same across the board; they are watching you.
Internet traffic travels in packets of information. Every single packet that comes from your network is sent out to your ISP to be routed to the Internet. Each packet is traversing your ISP's vast network of routers, switches, and servers just so you can reach a dot com.
Considering the amount of traffic that most ISPs process in just a single minute, all types of traffic from email, searches, and video chats, it is no wonder that we are willing to throw some serious money at the ISP just to stay connected. There is no denying these companies have a big job to do.
In these days of constant interconnectivity, it is easy to forget that internet access is a privilege and not a right. As a result, we are subject to the terms and conditions dictated by our ISP. For just about every provider out there, this includes logging and monitoring internet activity.
To understand why providers would log and monitor traffic, let’s step back in history to the Digital Millenium Copyright Act of 1998 (DMCA). Fresh off the heels of Napster turning the music industry upside down with its peer to peer file sharing of copyrighted music, President Clinton signed a piece of legislation that really brought about the age online of monitoring. While the DMCA was multi-faceted, one major focus was the liability exemption of ISPs from copyright infringement - if they aided in stopping it.
This gives IPSs all the motivation needed to start actively monitoring its users, because it exempts them from liability for its users actions. Not a bad setup if you are an ISP.
Truthfully, we do not know to what extent the ISPs are watching and monitoring individual users online activity. If you live in a place where the government controls the ISPs, like China, users should expect little to no privacy from their provider. Here in the US, it is a bit more nebulous and no one knows what the future holds for net privacy.
Recent Posts
-
What You Need to Know to Donate Safely Online
Cybersecurity has become an increasingly critical issue in the digital age. For instance, in 2016, m …Mar 10th 2022 -
What is a Default Gateway?
A default gateway is where all your internet traffic goes first before leaving your network. That’s …Jan 4th 2022 -
Essential Cybersecurity Tools Every Business Needs
IT infrastructures across organizations are now more complex than ever. Given the increasing number …Nov 29th 2021




